Έλεγχος
Διομήδης Σπινέλλης
Τμήμα Διοικητικής Επιστήμης και Τεχνολογίας
Οικονομικό Πανεπιστήμιο Αθηνών
dds@aueb.gr
Στόχοι του ελέγχου
"On January 23, 2003, a Singapore Airlines (SIA) Boeing 747-400 experienced
a complete loss of information on all six integrated display units (IDU) on
the flight deck instrument panels while in cruise flight from Singapore to
Sydney, Australia. The pilots flew the airplane for 45 minutes using standby
flight instruments while they communicated with SIA maintenance personnel
about the problem. SIA maintenance personnel advised the flight crew to pull
out then push back in (or cycle) the circuit breakers for the EFIS/EICAS
interface units (EIU), which returned the IDUs to normal operation. The
flight continued to Sydney and landed without further incident."
U.S. National Transportation Safety Board Recommendations A-03-55 and A-03-56 (http://www.ntsb.gov/Recs/letters/2003/A03_55_56.pdf)
Μια ακραία θεώρηση της διεργασίας του ελέγχου είναι η παρακάτω:
- Έλεγχος είναι η διεργασία εκτέλεσης του προγράμματος με σκοπό
να βρεθούν λάθη.
- Μια καλή περίπτωση ελέγχου είναι αυτή που έχει αυξημένη πιθανότητα
να βρει λάθος.
- Ένας επιτυχημένος έλεγχος είναι αυτός που βρήκε νέα λάθη.
Βασικές αρχές
- Κάθε έλεγχος πρέπει να αφορά μια συγκεκριμένη απαίτηση
- Η προετοιμασία των ελέγχων αρχίζει πολύ πριν την εκτέλεσή τους
- Αρχή του Pareto: 80% των λαθών θα αφορούν 20% των τμημάτων του λογισμικού
- Ο έλεγχος πρέπει να αρχίζει από τις μικρές δομικές μονάδες και να
καταλήγει στο ολοκληρωμένο σύστημα
- Δεν είναι δυνατό να ελεγχθεί ένα σύστημα πλήρως
- Ο αποτελεσματικός έλεγχος εκτελείται από τρίτους
Επαλήθευση και επικύρωση
Λογισμικό που μπορεί να ελεγχθεί
Για να μπορέσει το λογισμικό να ελεγχθεί αποτελεσματικά πρέπει να
πληροί τις παρακάτω προϋποθέσεις:
- Λειτουργικότητα
- Παρατηρησιμότητα
- Ελεγξιμότητα
- Αποσυνθεσιμότητα
- Απλότητα
- Ευστάθεια
- Τεκμηρίωση
Αναλυτικά:
- Λειτουργικότητα
- Λίγα λάθη
- Τα λάθη να μην εμποδίζουν τον έλεγχο
- Η ανάπτυξη υλοποιεί ολοκληρωμένες λειτουργίες (που μπορούν να ελεγχθούν)
- Παρατηρησιμότητα
- Κάθε είσοδος δημιουργεί διακριτά αποτελέσματα
- Η κατάσταση του συστήματος και των μεταβλητών του είναι ορατή
- Η προηγούμενη κατάσταση του συστήματος και των μεταβλητών του μπορεί να είναι ορατή (π.χ. από καταγραφές)
- Εύκολη ανίχνευση λανθασμένων αποτελεσμάτων
- Αυτόματη ανίχνευση εσωτερικών σφαλμάτων
- Αυτόματη αναφορά εσωτερικών σφαλμάτων
- Πρόσβαση στον πηγαίο κώδικα
- Ελεγξιμότητα
- Κάθε πιθανή έξοδος μπορεί να δημιουργηθεί με κατάλληλες εισόδους
- Όλος ο κώδικας μπορεί να εκτελεστεί με κατάλληλες εισόδους
- Ο ελεγκτής μπορεί να μεταβάλει άμεσα την κατάσταση του λογισμικού και του υλικού
- Η μορφή της εισόδου και της εξόδου είναι τακτική και ευνόητη
- Οι έλεγχοι είναι εύκολο να προδιαγραφούν, να αυτοματοποιηθούν
και να αναπαραχθούν.
- Αποσυνθεσιμότητα
- Το λογισμικό αποτελείται από ανεξάρτητα αρθρώματα
- Κάθε άρθρωμα μπορεί να ελεγχθεί αυτόνομα
- Απλότητα
- Λειτουργική απλότητα: δεν υπάρχουν περιττές λειτουργίες
- Δομική απλότητα: τα σφάλματα μπορούν να απομονωθούν σε
συγκεκριμένα αρθρώματα
- Απλότητα κώδικα: ο κώδικας μπορεί εύκολα να ελεγχθεί.
- Ευστάθεια
- Το λογισμικό δεν αλλάζει συχνά
- Οι αλλαγές στο λογισμικό ελέγχονται
- Οι αλλαγές δεν αναιρούν προηγούμενους ελέγχους
- Προβλήματα στο λογισμικό δεν το αχρηστεύουν
- Τεκμηρίωση
- Κατανοητό σχέδιο λογισμικού
- Κατανόηση της δομής του λογισμικού και των σχέσεων των τμημάτων του
- Τεκμηρίωση των αλλαγών
- Εύκολη πρόσβαση στην τεκμηρίωση
- Καλή οργάνωση της τεκμηρίωσης
Κατηγορίες ελέγχων
- Στατικές τεχνικές (δεν απαιτούν την εκτέλεση του προγράμματος)
- Δυναμικές τεχνικές (βασίζονται στην εκτέλεση του προγράμματος)
- Συμβολική εκτέλεση
- Δυναμικός έλεγχος
Στρατηγικές δυναμικού ελέγχου
Διακρίνουμε δύο τρόπους δυναμικού ελέγχου του λογισμικού:
- Στρατηγική μαύρου κουτιού (black box)
Ελέγχουμε το λογισμικό ως ένα σύστημα με γνωστές προδιαγραφές
αλλά άγνωστη υλοποίηση.
Μπορούμε έτσι να βρούμε:
- Λειτουργικότητα που απoυσιάζει ή που έχει υλοποιηθεί με
λανθασμένο τρόπο
- Λάθη διεπαφών
- Λάθη σε δομές δεδομένων και πρόσβαση στην εξωτερική βάση δεδομένων
- Προβλήματα απόδοσης
- Λάθη κατά την εκκίνηση και τον τερματισμό
- Στρατηγική άσπρου κουτιού (white box)
ή γυάλινου κουτιού (glass box)
Ελέγχουμε το λογισμικό με βάση την εσωτερική δομή του.
Μπορούμε έτσι να βρούμε:
- Λογικά λάθη σε μέρη του προγράμματος που σπάνια εκτελούνται
- Λάθη σε λογικές διαδρομές του προγράμματος που θεωρούμε πως
δε θα έπρεπε να εκτελούνται
- Τυπογραφικά λάθη σε μέρη του προγράμματος που σπάνια εκτελούνται
Δεν μπορούμε όμως να βρούμε:
- Μη συμμόρφωση με τις προδιαγραφές
- Μονοπάτια που απουσιάζουν
- Λάθη που αποκαλύπτονται με ειδικές τιμές δεδομένων
Στρατηγική μαύρου κουτιού
- Για διάστημα τιμών δοκιμάζουμε
την ελάχιστη επιτρεπτή και μέγιστη μη επιτρεπτή για το άνω
και κάτω όριο τιμών
- Για πλήθος στοιχείων δοκιμάζουμε το μικρότερο και μεγαλύτερο πλήθος
καθώς και ένα μικρότερο και ένα μεγαλύτερο από τον αριθμό αυτό
- Δημιουργούμε τιμές εισόδου που να παράγουν αντίστοιχες
αντιπροσωπευτικές τιμές από τα τελικά αποτελέσματα
Στρατηγική άσπρου κουτιού
- Κάθε εντολή να εκτελεστεί μια τουλάχιστο φορά.
- Κάθε συνθήκη πρέπει να ελέγχεται για κάθε συνδυασμό αληθών και
ψευδών τιμών.
- Κάθε βρόχος πρέπει να εκτελείται 0, 1, 2, n-1, n, και n+1 φορές.
Σχέδιο δυναμικού ελέγχου
- Ταυτότητα
- Εισαγωγή
- Στόχοι
- Υποδομή
- Έκταση του ελέγχου
- Παραπομπές
- Στοιχεία προς έλεγχο
- Χαρακτηριστικά που θα ελεγχθούν
- Χαρακτηριστικά που δε θα ελεγχθούν
- Μεθοδολογία
- Κριτήρια αποδοχής
- Κριτήρια αναστολής και απαιτήσεις επανάληψης
- Αναστολή ελέγχου
- Επανάληψη ελέγχων
- Παραδοτέα
- Εργασίες ελέγχου
- Περιβάλλον ελέγχου
- Ευθύνες
- Ομάδα διοίκησης ελέγχου
- Ομάδα ανάπτυξης
- Ομάδα ελέγχου
- Προσωπικό και εκπαίδευση
- Προσωπικό
- Εκπαίδευση
- Χρονοδιάγραμμα
- Αντιμετώπιση προβλημάτων
- Έγκριση
Οι έλεγχοι πραγματοποιούνται με βάση την παρακάτω τεκμηρίωση:
- Προδιαγραφές σχεδίου ελέγχου
- Προδιαγραφές περίπτωσης ελέγχου
- Αναγνωριστικό
- Τμήματα που θα δοκιμαστούν
- Καθορισμός εισόδων
- Καθορισμός αναμενόμενων αποτελεσμάτων
- Ανάγκες περιβάλλοντος
- Διαδικαστικές απαιτήσεις
- Εξαρτήσεις
- Προδιαγραφές διαδικασίας διεκπεραίωσης ελέγχου
- Έκθεση διαβίβασης οντοτήτων προς έλεγχο
- Ημερολόγιο ελέγχου
- Περιληπτική έκθεση ελέγχου
Αυτοματοποιημένος έλεγχος
- Πρέπει να προσπαθούμε οι έλεγχοι να εκτελούνται αυτόματα
- Έτσι μπορούν να εκτελούνται μετά από κάθε αλλαγή στο λογισμικό
- Έλεγχοι δομικών μονάδων μπορούν να περιλαμβάνονται στον κώδικα του
προγράμματος.
Παράδειγμα (με τη χρήση της κλάσης της Java Junit):
public class MoneyTest extends TestCase {
private Money f12CHF;
private Money f14CHF;
private Money f28USD;
protected void setUp() {
f12CHF= new Money(12, "CHF");
f14CHF= new Money(14, "CHF");
f28USD= new Money(28, "USD");
}
}
public void testMoneyMoneyBag() {
// [12 CHF] + [14 CHF] + [28 USD] == {[26 CHF][28 USD]}
Money bag[]= { f26CHF, f28USD };
MoneyBag expected= new MoneyBag(bag);
assertEquals(expected, f12CHF.add(f28USD.add(f14CHF)));
}
public static Test suite() {
TestSuite suite= new TestSuite();
suite.addTest(new MoneyTest("testMoneyEquals"));
suite.addTest(new MoneyTest("testSimpleAdd"));
return suite;
}
- Αυτοματοποιημένοι έλεγχοι μπορούν να εκτελούνται μαζικά με
τη βοήθεια εργαλείων:
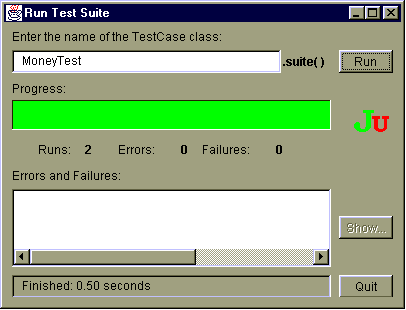
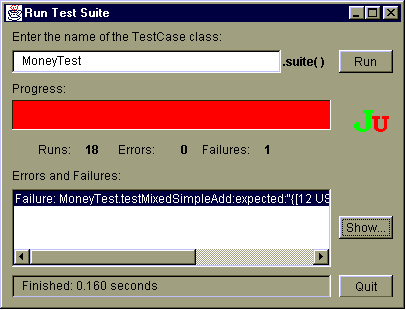
Διαχείριση λαθών
Η διαχείριση των λαθών πρέπει να γίνεται οργανωμένα.
Σε αυτό απαραίτητη είναι μια ΒΔ ή ένα ειδικό πρόγραμμα.
Για κάθε σφάλμα ή πρόβλημα είναι χρήσιμα τα παρακάτω στοιχεία:
- Κωδικό αριθμό
- Τίτλο
- Πρόσωπο που το διαπίστωσε
- Σοβαρότητα
- Είδος (λάθος, πρόταση βελτίωσης, μη συμμόρφωση με της προδιαγραφές, χρηστικότητα κ.λπ.)
- Περιβάλλον
- Αναλυτική περιγραφή
- Συνοδευτικά στοιχεία
- Υποσύστημα
- Ημερομηνία εισαγωγής στο σύστημα
- Υπεύθυνος αποκατάστασης
- Ημερομηνία ανάθεσης
- Ημερομηνία αποκατάστασης
- Προτεραιότητα
- Σημειώσεις
- Αλλα σχετικά λάθη
- Κατάσταση (ανοιχτό, κλειστό, υπό εξέταση, δε διαπιστώθηκε)
- Έκδοση του κώδικα που εμφανίστηκε
- Έκδοση του κώδικα που διορθώθηκε
Βιβλιογραφία
- Εμμανουήλ Σκορδαλάκης.
Εισαγωγή στην Τεχνολογία Λογισμικού, σελίδες 133-155.
Εκδόσεις Συμμετρία, 1991.
- Εμμ. Α. Γιακουμάκης
Τεχνολογία Λογισμικού: Κωδικοποίηση, έλεγχος και συντήρηση λογισμικού.
σελίδες 55-157.
Εκδόσεις Α. Σταμούλης, Αθήνα, Πειραιάς, 1993.
- Kent Beck and Erich
Gamma.
Test infected: Programmers love writing tests.
Java Report, July 1998.
- Watts S. Humphrey.
Managing the Software Process, pages 171–223.
Addison-Wesley, 1989.
- IEEE standard for
software verification and validation plans.
Published by the American National Standards Institute, 1430 Broadway, New
York, New York 10018, February 1987.
ANSI/IEEE Std 1012-1986.
- Institute of Electrical and
Electronics Engineers, Inc., New York, NY, USA.
Software Test Documentation, 1998.
IEEE Standard 829-1998.
- Cem Kaner, Jack Falk, and
Hung Quoc Nguyen.
Testing Computer Software.
Wiley, 1999.
- Roger S. Pressman.
Software Engineering: A Practitioner's Approach, pages 468–522.
McGraw-Hill, 1987.
- Roger S. Pressman.
Software Engineering: A Practitioner's Approach, pages 426–493.
McGraw-Hill, fifth edition, 2000.
European Adaptation. Adapted by Darrel Ince.
- Ian Sommerville.
Software Engineering, pages 419–466.
Addison-Wesley, sixth edition, 2001.
Παράρτημα: έλεγχοι συμμόρφωσης στο σύστημα Windows
Κατά τη Microsoft ή συμμόρφωση ενός προγράμματος με το λειτουργικό
σύστημα Windows πρέπει να ελέγχεται με τα παρακάτω κριτήρια:
1 Set Up the Application
1.1 Setup program should start when CD is inserted.
1.2 Setup should also run from:
1.2.1 Control Panel's add/remove programs applet (Application Manager).
1.2.2 Taskbar's Start.Run.
1.2.3 Command line.
1.2.4 Windows Explorer (double-click the Setup program in Windows Explorer).
1.2.5 Off the Internet (as a self-extracting executable).
1.3 Aborting Setup, exiting or canceling Setup before completion should mean that:
1.3.1 Temp directories are removed.
1.3.2 Registry is rolled back (if changed).
1.3.3 No files are installed.
1.3.4 No system files are updated.
1.3.5 No program groups or folders are left on the Start menu.
1.4 Setup options should include:
1.4.1 Change name of install directory.
1.4.2 Install to compressed directory.
1.4.3 Install on a drive different from the OS. (Install application on a FAT32 drive if Windows NT is installed on NTFS, for example.)
1.4.4 Install on a system where the OS is not on C.
1.4.5 Install on a system that has no autoexec.bat or config.sys in the root of C.
1.4.6 Installation options to test:
1.4.6.1 Choose "full" or "complete" to make sure everything installs.
1.4.6.2 Choose partial options, to make sure core parts of the application are still installed.
1.4.6.3 Rerun Setup to add options not installed during the partial installation, and verify that those options have been added.
1.4.6.4 Update/patch installation from the Internet, if files are available.
1.4.6.5 Administrative installation: Install on a server, and then test a local workstation installation.
1.5 Setup should detect the following environment variables:
1.5.1 The current version of Windows.
1.5.2 A previous installation of the same application.
1.5.3 Earlier versions of the application. (Setup should upgrade these.)
1.5.4 Other, possibly newer, versions of applications it integrates with. (Test installation on machines with newest versions of Office suites and browsers, for example.)
1.5.5 Disk space, including:
1.5.5.1 Drives with "not enough" space.
1.5.5.2 Very large drives (more than 8 gigabytes [GB]).
1.5.5.3 Removable media (ZIP, Jazz).
1.5.6 The presence or absence of sound cards and other special hardware. (Setup should then select the correct installation options.)
1.5.7 Fonts:
1.5.7.1 Verify that installed fonts are visible in \Fonts folder (Control Panel).
1.5.7.2 Verify installed fonts in other applications (WordPad, Office suites).
1.5.7.3 Print hard copy using fonts and verify.
1.6 Program group/folder tests should verify that:
1.6.1 The "Change default name" option works.
1.6.2 All expected links (icons) appear.
1.6.3 All links (icons) work.
1.6.4 Only one group/folder is created.
1.7 If the installation continues across two or more CDs:
1.7.1 The installation should proceed without user intervention after the user mounts the next CD.
1.7.2 If the application accesses content on the CDs (such as Clipart) after installation, open representative files from each CD, using:
1.7.2.1 The same CD drive used to install the application.
1.7.2.2 A separate CD drive for data CDs.
1.7.2.3 Two or more drives for data CDs simultaneously.
1.8 Uninstall should:
1.8.1 Be available from Control Panel's add/remove programs applet (Application Manager).
1.8.2 Remove all program files and folders.
1.8.3 Remove all registry entries.
1.8.4 Remove the program group/folder.
1.8.5 Retain all shared files.
1.8.6 Retain all system files.
2 Start the Application
2.1 From a Start program/shortcut.
2.2 From Start, Run.
2.3 From an Explorer icon/shortcut.
2.4 From a desktop icon/shortcut.
2.5 From a command line.
2.6 By double-clicking the icon of a file associated with the application.
2.7 From a shortcut in the Startup group:
2.7.1 From a personal or common group on reboot.
2.7.2 From a common group only when changing logged-on user.
2.8 As service (when applicable):
2.8.1 Manual, automatic, disabled.
2.8.2 Log on as system account.
2.8.3 Log on as specific user:
2.8.3.1 With that user logged on.
2.8.3.2 With a different user logged on.
2.9 As a Darwin-aware application (when applicable):
2.9.1 Advertised.
2.9.2 Published.
2.10 As a second instance of the same app
3 Close the Application
3.1 Using File.Close or app's equivalent.
3.2 Using the Close button.
3.3 Using the system menu and accelerator.
3.4 From the minimized icon on the taskbar.
3.5 From the tray icon (for tray-enabled applications).
3.6 From system shutdown:
3.6.1 No dialog should appear if no "documents" are open and unsaved.
3.6.2 If unsaved "documents" are open, the user should be prompted to save them.
4 Run the Application
4.1 File I/O:
4.1.1 Open sample documents that ship with the application, or make several documents and use them in future testing.
4.1.2 Save each document in each supported format using Long File Names (max path name length, using all legal naming characters) to:
4.1.2.1 Local drives:
4.1.2.1.1 NTFS drives:
4.1.2.1.1.1 Compressed
4.1.2.1.1.2 Uncompressed
4.1.2.1.1.3 Encrypted
4.1.2.1.1.4 Through reparse point to local machine
4.1.2.1.1.5 Through reparse point to remote share
4.1.2.1.2 FAT16 drives
4.1.2.1.3 FAT32 drives
4.1.2.2 Remote (network) machines mapped to drive letters:
4.1.2.2.1 NTFS drives:
4.1.2.2.1.1 Compressed
4.1.2.2.1.2 Uncompressed
4.1.2.2.1.3 Encrypted
4.1.2.2.1.4 Through reparse point to local machine
4.1.2.2.1.5 Through reparse point to remote share
4.1.2.2.2 FAT16 drives
4.1.2.2.3 FAT32 drives
4.1.2.2.4 Win9x systems
4.1.2.2.5 Netware network
4.1.2.2.6 Macintosh systems
4.1.2.2.7 Other operating systems (if mounting systems are available)
4.1.2.3 Remote (network) machines using UNC (Uniform Naming Convention):
4.1.2.3.1 NTFS drives:
4.1.2.3.1.1 Compressed
4.1.2.3.1.2 Uncompressed
4.1.2.3.1.3 Through reparse point to local machine
4.1.2.3.1.4 Through reparse point to remote share
4.1.2.3.2 FAT16 drives
4.1.2.3.3 FAT32 drives
4.1.2.3.4 Win9x systems
4.1.2.3.5 Netware network
4.1.2.3.6 Macintosh systems
4.1.2.3.7 Other operating systems (if mounting systems are available)
4.1.3 Open each of the saved documents from each drive or share:
4.1.3.1 Verify that document is unchanged from the original.
4.1.3.2 Change the document, resave, reopen, and verify changes.
4.1.4 Open (create), save, reopen, and verify special-case files, including:
4.1.4.1 Very small (zero length) files.
4.1.4.2 Very large files.
4.1.4.3 Files in formats not native to the application.
4.1.4.4 Damaged or misnamed files.
4.1.4.5 Files the application can recognize from earlier versions or other applications.
4.1.5 Open a large number of files:
4.1.5.1 In MDI applications:
4.1.5.1.1 Cascade windows.
4.1.5.1.2 Tile windows.
4.1.5.1.3 Minimize windows.
4.1.5.1.4 Switch among windows.
4.1.5.2 Verify that Most Recently Used file lists behave as expected.
4.1.5.3 Verify Close All, if implemented.
4.1.6 Open by drag/dropping file icons onto open application window.
4.2 Printing
4.2.1 Create or open sample documents that contain the following, if supported:
4.2.1.1 Text in various sizes, styles and colors using:
4.2.1.1.1 TrueType fonts, including at least one font not resident on attached printers.
4.2.1.1.2 Postscript fonts.
4.2.1.1.3 Printer resident fonts.
4.2.1.2 Rotated text.
4.2.1.3 Reversed text.
4.2.1.4 Plain and reversed text:
4.2.1.4.1 On top of other text.
4.2.1.4.2 Under other text.
4.2.1.4.3 On top of other lines created by application.
4.2.1.4.4 Under other lines created by application.
4.2.1.4.5 On top of other graphics.
4.2.1.4.6 Under other graphics.
4.2.1.5 Graphics:
4.2.1.5.1 Vector
4.2.1.5.2 Bitmap
4.2.1.5.3 Scripted (.wmf files, for example)
4.2.1.5.4 Opaque and transparent backgrounds
4.2.1.5.5 Rotated graphics
4.2.1.5.6 Graphics that extend off the edge of the page
4.2.1.5.7 Graphics framed and cropped by the app
4.2.1.6 Objects drawn by the application (arrows, lines, borders, shapes):
4.2.1.6.1 Thick objects
4.2.1.6.2 Thin objects (hairlines)
4.2.1.6.3 Hatching, dotted, dashed, solid colors and grays
4.2.1.7 Objects embedded from other OLE/COM servers.
4.2.2 Print each sample to printers with Long File Names (printer names include all legal Long File Name characters and are at least 128 characters long):
4.2.2.1 Ink jet
4.2.2.2 PostScript black
4.2.2.3 PostScript printer
4.2.2.4 Non-Postscript black laser
4.2.2.5 Non-Postscript color laser
4.2.2.6 Fax
4.2.2.7 Special printers supported by the application (pen plotters, for example)
4.2.2.8 Local printers created from network print servers
4.2.2.9 Printers connected from net servers
4.2.2.10 Set properties and print in the following formats:
4.2.2.10.1 Landscape
4.2.2.10.2 Portrait
4.2.2.10.3 Rotated
4.2.2.10.4 Duplex
4.2.2.10.5 Enlarged/reduced
4.2.2.10.6 Stapled/collated
4.2.2.10.7 Color as black-and-white
4.3 Normal Windows user actions:
4.3.1 Check all menus.
4.3.1.1 Open documents or perform other actions that expose new menus. (For example, some applications do not show menus or disable/gray-out choices unless objects are selected on a document.)
4.3.1.2 Open all second-level and lower-level menus.
4.3.1.3 Choose menu options and verify results using:
4.3.1.3.1 Menu command.
4.3.1.3.2 Access key (Alt+underlined-letter).
4.3.1.3.3 Accelerator. (For example, Ctrl+O often performs File.Open.)
4.3.1.4 Toggle and verify checked menu commands.
4.3.1.5 Tear off and float menus (if supported).
4.3.1.6 Add and remove menu commands (if supported).
4.3.1.7 Close and reopen the application, verify persistence of menu changes.
4.3.2 Test dialogs:
4.3.2.1 Resize (if supported) and look for text clipping or controls that overlap.
4.3.2.2 Move dialog over application and off application to desktop and other running applications, verify repainting.
4.3.2.3 Test all controls for "normal" operation. (Note: Many controls can have restricted behaviors on some dialogs by design and custom controls that simulate standard Windows controls may have unusual behaviors, by design.)
4.3.2.3.1 Enter unexpected text in Edit boxes .
4.3.2.3.2 Move scroll bars and spin controls to extreme limits.
4.3.2.3.3 Click check boxes several times to toggle states.
4.3.2.3.4 Only one option (radio) button in a group should be "set" at any time, although by default all may be un-set when a dialog opens.
4.3.2.3.5 Select several contiguous and discontiguous items in multiline list boxes.
4.3.2.3.6 Select several different items in sequence from combo boxes.
4.3.2.3.7 Click header controls to change sort order of lists.
4.3.2.3.8 Right-click in all dialogs at several places. Any context menus that appear should make sense in the context of the dialog and click location. (For example, the "copy," "cut," "clear," and "delete" commands, if present, should be disabled or grayed out if nothing is selected.)
4.3.2.3.9 Click on areas that do not look like controls to verify that nothing happens.
4.3.2.4 Check all labels (static text) for clipping or truncated strings.
4.3.2.5 Check appearance of bitmaps that are not controls.
4.3.2.6 Close the dialog using:
4.3.2.6.1 OK button.
4.3.2.6.2 Cancel button.
4.3.2.6.3 Close button.
4.3.2.6.4 System menu and accelerator (usually Ctrl+F4).
4.3.2.6.5 Escape key.
4.3.3 Test toolbars:
4.3.3.1 Show/hide toolbars.
4.3.3.2 Verify that buttons' states (either enabled or grayed-out) track the state of the application.
4.3.3.3 Show/hide text.
4.3.3.4 Change size, style of icons/bitmaps.
4.3.3.5 Tear off/dock (on all edges).
4.3.3.6 Overlap.
4.3.3.7 Move off parent application's window.
4.3.3.8 Resize, verify expected button behavior (some buttons disappear off the end of the toolbar, others warp to multiple lines).
4.3.3.9 Customize:
4.3.3.9.1 Remove buttons.
4.3.3.9.2 Add buttons.
4.3.3.9.3 Change button sequence.
4.3.3.9.4 Change button properties:
4.3.3.9.4.1 Bitmap/icon.
4.3.3.9.4.2 Text.
4.3.3.9.4.3 Action the button controls.
4.3.3.10 Close the application, reopen, and verify that the expected toolbar preferences persist.
4.4 Editing functions
4.4.1 Select, using:
4.4.1.1 Menu (Select All).
4.4.1.2 Context menu.
4.4.1.3 Accelerators (Ctrl+A).
4.4.1.4 Mouse (click, drag).
4.4.1.5 Arrow keys.
4.4.2 Copy/cut/paste:
4.4.2.1 From Menus.
4.4.2.2 From Toolbars.
4.4.2.3 Using Windows accelerators (Ctrl+C and Ctrl+Insert for Copy, and so on).
4.4.2.4 Using context (right-click) menus.
4.4.2.5 From other applications via the Clipboard (including text and graphics).
4.4.2.6 To other applications (including text and graphics).
4.4.3 Move items, using:
4.4.3.1 Mouse (click, drag).
4.4.3.2 Arrow keys.
4.4.4 Delete items, (and verify they are not on the Clipboard), using:
4.4.4.1 Menu.
4.4.4.2 Context menu.
4.4.4.3 Accelerators.
4.4.4.4 Mouse (click, drag).
4.4.4.5 Arrow keys.
4.4.5 Test editing with application's Clipboard (if it's separate from the Windows Clipboard).
4.5 OLE, ActiveX, COM, DCOM:
4.5.1 Test containers with objects from a variety of servers.
4.5.2 Drag/drop embedded objects from servers to containers.
4.5.3 Use Insert or Paste.Special to embed objects in containers (test all variations); If the test application is an OLE/ActiveX server, insert its objects in other containers.
4.5.4 In all documents with embedded objects, launch the servers from the objects:
4.5.4.1 Test editing the objects in place.
4.5.4.2 Test saving the objects in place.
4.5.5 Save and reopen documents with embedded objects, verify results.
4.5.6 Print documents with embedded objects, verify results.
4.6 Appearance
4.6.1 Test at various color depths (watch for changes in bitmaps on dialogs and toolbars, especially when grayed-out); test at various resolutions.
4.6.2 Test maximize, minimize, restore/resize.
4.6.3 Test with Taskbar:
4.6.3.1 Select "Always on top" option.
4.6.3.2 Select "Autohide" option.
4.6.3.3 Show/hide clock.
4.6.3.4 Dock the taskbar to all four sides of desktop.
4.6.3.5 Make the taskbar larger (more rows/columns) than standard size.
4.6.3.6 For applications that switch to full-screen mode (such as presentations applications) verify that taskbar appears normally after application returns from full-screen mode.
4.6.4 Move the application over and under other running applications' windows to verify all for proper repainting.
4.6.5 Test with "always on top" toolbars and trays from other applications, such as Office suites.
4.6.6 Test on multiple monitors:
4.6.6.1 Use at least two monitors, one offset below and to the right of the other.
4.6.6.2 Use each available monitor as the primary monitor.
4.6.6.3 Maximize the application on each monitor.
4.6.6.4 Drag across multiple monitors.
4.6.6.5 Verify that dialogs from the application do appear on parts of the virtual monitor not represented by real monitor screens, where the user cannot reach them with the mouse.
4.6.6.6 Test left- and right-mouse clicks on all dialogs and application surfaces on all monitors for all combinations.
4.6.6.7 Move the taskbar so it sits on divisions between the monitors.
4.6.6.8 Float all possible application elements off the parent's monitor to other monitors; Verify that all toolbar and other functions still work.
4.6.6.9 Test animation such as graphics rotations, drawing rendering, movies and screen savers across all monitors.
4.7 Help:
4.7.1 Open Help, using:
4.7.1.1 Menu commands.
4.7.1.2 The toolbar.
4.7.1.3 Context menus, if supported.
4.7.1.4 F1.
4.7.1.5 Shift+F1.
4.7.2 Verify all supported:
4.7.2.1 Bookmarks.
4.7.2.2 Annotations.
4.7.2.3 Search Index.
4.7.2.4 Links.
4.7.2.5 Scrolling.
4.7.2.6 Special functions and controls, such as buttons.
4.7.3 Open all supported Help files, including files from other applications, if linked.
4.8 Supported hardware:
4.8.1 Scanners:
4.8.1.1 Twain
4.8.1.2 SCSI
4.8.1.3 Parallel
4.8.1.4 Serial
4.8.1.5 USB
4.8.2 Tape drives:
4.8.2.1 SCSI
4.8.2.2 Parallel
4.8.2.3 IDE
4.8.2.4 USB
4.8.2.5 Proprietary driver hardware
4.8.3 Video:
4.8.3.1 Cameras
4.8.3.2 Editing/frame capture
4.8.3.3 Tuner
4.8.4 Sound:
4.8.4.1 Playback
4.8.4.2 Record
4.8.4.3 Tuner
4.8.5 Telephony devices:
4.8.5.1 POTS Modems
4.8.5.2 ISDN
4.8.5.3 ADSL
4.8.6 Pointing devices:
4.8.6.1 Touch pads
4.8.6.2 Touch screens
4.8.6.3 Mice with multiple buttons and wheels
4.8.6.4 Trackballs and mice requiring special drivers
4.8.7 Mass storage:
4.8.7.1 Removable drives:
4.8.7.1.1 SCSI
4.8.7.1.2 IDE
4.8.7.1.3 Parallel
4.8.7.1.4 USB
4.8.7.1.5 CD-R/W
4.8.7.1.6 SCSI
4.8.7.1.7 IDE
4.8.7.1.8 USB
4.8.8 IRDA
4.9 Special functions:
4.9.1 Send to.
4.9.2 Launch applications from toolbars.
4.9.3 Run in background, or as service, or scheduled. (Test other applications with background services/systems running.)
4.9.4 Export to HTML. (Test resulting HTML with common browsers and other apps that can read or import HTML.)
4.9.5 Databases:
4.9.5.1 Concurrent user access, file locking.
4.9.5.2 Complex queries.
4.9.6 Other application-specific functions
Ασκήσεις
- Περιγράψτε τις τιμές εισόδου για κάθε συνάρτηση για να ελεγχθεί ο παρακάτω κώδικας:
int
min(int t1, int t2)
{
return t2 > t1 ? t1 : t2;
}
int
max(int t1, int t2)
{
return t1 > t2 ? t1 : t2;
}
int
min(int t1, int t2, int t3)
{
return min(min(t1, t2), t3);
}
int
max(int t1, int t2, int t3)
{
return max(max(t1, t2), t3);
}
int
range(int min, int max, int val)
{
return min(max(min, val), max);
}
- Γράψτε ένα πρόγραμμα ελέγχου για τις παραπάνω συναρτήσεις
- Δοκιμάστε τη χρήση της κλάσης JUnit
- Υλοποιήστε στη ΒΔ Access ένα απλό σύστημα παρακολούθησης λαθών


