Web Security and Mobile Code
Diomidis Spinellis
Department of Management Science and Technology
Athens University of Economics and Business
Athens, Greece
dds@aueb.gr
Web Security Requirements
- Confidentiality (client and server)
- Integrity (client and server)
- Availability (mostly server issue)
User Privacy: What are we Protecting?
- Identity (name, email)
- Location (IP address, domain name, physical location)
- Visited sites
- Search engine input
- Shopping habits
- Form data
Data Traces
Traces are left on:
- Address-bar history
- Local history file
- Local cache
- Cookie file
- Explicitly set proxy log file
- Transparent proxy log file
- Remote log files
- Remote databases
- Packet tracing dumps
Web Server Data
Typical data available to the web server:
GET http://www.google.com/ HTTP/1.1
Host: www.google.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 5.1; en-US; rv:1.6) Gecko/20040113
Accept: application/x-shockwave-flash,text/xml,application/xml,application/xhtml+xml,text/html;q=0.9,text/plain;q=0.8,image/png,image/jpeg,image/gif;q=0.2,*/*;q=0.1
Accept-Language: en-us,en;q=0.8,el;q=0.5,de;q=0.3
Accept-Encoding: gzip,deflate
Accept-Charset: windows-1253,utf-8;q=0.7,*;q=0.7
Keep-Alive: 300
Proxy-Connection: keep-alive
Cookie: PREF=ID=33a5ab74b4a12719:LD=en:CR=2:TM=1070012757:LM=1070012764:S=bEOIfrJZzBGyc5LD
Log File Contents
Normal Users
217.195.129.242 - - [23/Jun/2004:15:38:25 +0300] "GET /pubs/jrnl/2000-IST-Components/html/comp.html HTTP/1.0" 200 49099 "http://find.in.gr/results.page?data=unix+command" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1; Q312461)"
217.195.129.242 - - [23/Jun/2004:15:38:25 +0300] "GET /pubs/jrnl/2000-IST-Components/html/process.gif HTTP/1.0" 200 6429 "http://www.spinellis.gr/pubs/jrnl/2000-IST-Components/html/comp.html" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1; Q312461)"
backport.reaktor-i.com - - [23/Jun/2004:16:00:05 +0300] "GET /sw/umlgraph/doc/index.html HTTP/1.1" 200 3317 "http://www.spinellis.gr/sw/umlgraph/" "Mozilla/5.0 (X11; U; Linux i686; en-US; rv:1.6) Gecko/20040207 Firefox/0.8"
backport.reaktor-i.com - - [23/Jun/2004:16:00:08 +0300] "GET /sw/umlgraph/doc/cd-intro.html HTTP/1.1" 200 2188 "http://www.spinellis.gr/sw/umlgraph/doc/index.html" "Mozilla/5.0 (X11; U; Linux i686; en-US; rv:1.6) Gecko/20040207 Firefox/0.8"
Crawler
65.197.137.37 - - [22/Jun/2004:13:33:58 +0300] "GET /robots.txt HTTP/1.1" 200 35 "-" "ZipppBot/0.25 (Zippp; http://www.zippp.net; webmaster@zippp.net)"
65.197.137.37 - - [22/Jun/2004:13:33:59 +0300] "GET /pubs/conf/1994-OOPSLA-Multipar/html/mlom.html HTTP/1.1" 200 19166 "-" "ZipppBot/0.25 (Zippp; http://www.zippp.net; webmaster@zippp.net)"
Web Server Exploitation Attempts
[Thu Jun 10 11:36:59 2004] [error] [client 148.244.150.52] script not found or unable to stat: /webdata/istlab-cgi-bin/FormMai
l.pl
[Thu Jun 10 11:37:03 2004] [error] [client 148.244.150.52] script not found or unable to stat: /webdata/istlab-cgi-bin/mail.pl
[Thu Jun 10 11:37:03 2004] [error] [client 148.244.150.52] script not found or unable to stat: /webdata/istlab-cgi-bin/Mail.pl
[Thu Jun 10 11:37:04 2004] [error] [client 148.244.150.52] script not found or unable to stat: /webdata/istlab-cgi-bin/Form.pl
[Thu Jun 10 11:37:04 2004] [error] [client 148.244.150.52] script not found or unable to stat: /webdata/istlab-cgi-bin/form.pl
[Fri Jun 18 23:05:25 2004] [error] [client 216.245.167.136] File does not exist: /webdata/spinellis/_vti_bin/owssvr.dll
[Fri Jun 18 23:05:25 2004] [error] [client 216.245.167.136] File does not exist: /webdata/spinellis/MSOffice/cltreq.asp
[Fri Jun 18 23:06:17 2004] [error] [client 216.245.167.136] File does not exist: /webdata/spinellis/_vti_bin/owssvr.dll
[Fri Jun 18 23:06:18 2004] [error] [client 216.245.167.136] File does not exist: /webdata/spinellis/MSOffice/cltreq.asp
Packet Dump Output
Web Request
02:40:27.881867 192.168.238.1.1540 > 192.168.238.5.www: P 1:485(484) ack 1 win 6
4240 (DF)
0x0000 4500 020c 5af0 4000 8006 40a3 c0a8 ee01 E...Z.@...@.....
0x0010 c0a8 ee05 0604 0050 6a19 984a 87b4 aae9 .......Pj..J....
0x0020 5018 faf0 59b7 0000 4745 5420 2f6f 7267 P...Y...GET./org
0x0030 616e 2d65 6e68 616e 6365 6d65 6e74 2e68 an-enhancement.h
0x0040 746d 6c20 4854 5450 2f31 2e31 0d0a 486f tml.HTTP/1.1..Ho
0x0050 7374 3a20 3139 322e 3136 382e 3233 382e st:.192.168.238.
0x0060 350d 0a55 7365 722d 4167 656e 743a 204d 5..User-Agent:.M
0x0070 6f7a 696c 6c61 2f35 2e30 2028 5769 6e64 ozilla/5.0.(Wind
Password in a Packet Dump
05:50:03.157394 seagull.spinellis.gr.1098 > www.taxisnet.gr.http: P
479:588(109) ack 1 win 16603 (DF)
0x0000 4500 0095 0654 4000 8006 7057 c0a8 880e E....T@...pW....
0x0010 d4cd 6633 044a 0050 fdf4 e5a9 912f e6a5 ..f3.J.P...../..
0x0020 5018 40db 1033 0000 436f 6e74 656e 742d P.@..3..Content-
0x0030 7479 7065 3a20 6170 706c 6963 6174 696f type:.applicatio
0x0040 6e2f 782d 7777 772d 666f 726d 2d75 726c n/x-www-form-url
0x0050 656e 636f 6465 640d 0a43 6f6e 7465 6e74 encoded..Content
0x0060 2d6c 656e 6774 683a 2033 380d 0a0d 0a70 -length:.38....p
0x0070 7764 3d73 6563 7265 7426 7573 6572 6e61 wd=secret&userna <<<
0x0080 6d65 3d74 6573 7475 7365 7226 7061 7373 me=testuser&pass <<<
0x0090 776f 7264 3d word=
Malicious Applets
Once malicious code gets control of the machine it can:
- Compromise the user's privacy
- Actively snoop the user's keystrokes
- Steal resources to:
- Orchestrate a DDoS attack
- Send spam mail
- Spread viruses
- Dial long-distance calls
- Impersonate on behalf of the user (including certificate authentication)
- Distribute sensitive documents
The Java Sandbox Model
- Java code is executed through a virtual machine
- Java applets can contain untrusted code
- Untrusted code is checked for validity
- Untrusted code is executed in a sandbox using an appropriate security policy
Bytecode Verification
Bytecode verification checks that:
- The file is correctly formatted
- The parameter stack will not overflow or underflow
- Bytecode instructions use the correct types
- No invalid type conversions are performed
- No unauthorised member access is performed (through private or protected fields and methods).
- Register accesses follow the legal conventions
Common problems
- Insecure Java implementation (e.g. type checking)
- Inappropriate security policy
Policy Example
As an example the sanbox policy may prohibit:
- Reading local files
- Writing local files
- Deleting local files
- Renaming local files
- Creating directories
- Reading directory contents
- Network connections to machines other than the applet's source
- Waiting for network connections
- Creating new windows
- Changing system settings
- Loading dynamic libraries
- Creating a new clall loader or security manager
- Creating classes that already exist
ActiveX and Code Signing
- ActiveX applets are based on Microsoft's
Component Object Model (COM)
- ActiveX applets can access all the machine's resources
- They are signed with a digital signature to ensure their origin.
- A similar option is also offered for Java code
- Users are supposed to trust signed applets as they trust
retail software
Problems:
- All or nothing proposition
- Who do you trust?
- Programs from trusted sources may contain vulnerabilities
- Programs from trusted sources may unknowingly contain
malicious code (e.g. by linking with a library)
Javascript
- No relation to Java
- Interpreted inside the browser
- Browser and its limited runtime environment act as a sandbox
- Security problems
Exploitation examples:
- Show pop-up windows
- Access the history file
- Read directory contents
- Trick user to send files by email to untrusted sources
- Violate firewall security policies (e.g. by recreating an applet tag)
Cookies
- Needed to maintain state in stateless HTTP
- Useful for e-commerce (e.g. implementing a shopping basket)
- Format:
Name=VALUE; expires=DATE; domain=DOMAIN; path=PATH; secure
- Example:
www.in.gr FALSE / FALSE 2051222309 SITESERVER ID=8b048791364ee52dfc1d627045d5c58c
.google.com TRUE / FALSE 2147361448 PREF ID=33a5ab94b4a12719:LD=en:CR=2:TM=1070212757:LM=1074012764:S=bEbIgrJZzBGyc5LD
.yahoo.com TRUE / FALSE 1271361609 U mt=Kl4g_p8MhYuN9bHjdexUb81uQuDrHYcx_oFi1Q--&ux=Sqf7/A&un=febgmfte1juft
- Only the same host can access a cookie
Security problems
- The cookie file stores unencrypted personal data over an extended period
- Can be subverted by DNS spoofing
- Therefore an attacker can access personal data (e.g. shopping habits)
- Other users of a machine can access the cookie file
- Problems when cookies are used to make authorisation easier
User Authentication
- The basic authentication method transmits the password unencrypted
Example
POST /cgi-bin/smswww HTTP/1.0
Referer: http://www.netcs.com/pages/foo/send.html
Proxy-Connection: Keep-Alive
User-Agent: Mozilla/3.01 (Win95; I)
Host: www.netcs.com
Accept: image/gif, image/x-xbitmap, image/jpeg, image/pjpeg, */*
Content-type: application/x-www-form-urlencoded
Content-length: 143
Authorization: Basic aWV0ZopqZXRm
- Only useful for "advisory locks"
- Better authentication should be implemented through an SSL link and
custom application code
- Cookies should not be used for authentication
Application-layer Attacks
- Scripting vulnerabilities
- Buffer overflows
- Cookie poisoning
- Hidden field manipulation
- Parameter tampering
- Cross-site scripting
- SQL injection
Server Security and Scripting
- Server-side scripting (ASP, PHP, mod_perl, CGI) uses interpreted languages
(Visual Basic, PHP, sh, Perl, Tcl, Java, Python)
- Can be used by attackers to execute code on the server
- Compromise the web server (e.g. change security model)
- Compromise the database
- Compromise the host
Scripting Exploitation Example
The following flawed and insecure Perl program is
supposed to run the Unix "finger" command for the user
given on a form's USER field:
#!/usr/bin/perl
$query = $ENV{'QUERY_STRING'};
@pairs = split(/\&/, $query);
for (@pairs) {
($field, $val) = split(/=/);
$field =~ s/\+/ /g;
$field =~ s/\%(\w\w)/sprintf("%c", hex($1))/eg;
$val =~ s/\+/ /g;
$val =~ s/\%(\w\w)/sprintf("%c", hex($1))/eg;
$field{$field} = $val;
}
$|=1;
print "Content-Type: text/plain\n\n";
system "finger $field{USER}\n";
Running the program with USER having the value "dds"
http://www.host.gr/cgi-bin/pe?USER=dds
will give the following result:
Login: dds Name: Diomidis Spinellis
Directory: /home/dds Shell: /bin/bash
On since Wed Jun 30 12:18 (EET) on ttyp0
5 minutes 49 seconds idle
Adding to the URI a semicolon (the Unix shell command separator)
and the command cat /etc/shadow
http://www.host.gr/cgi-bin/pe?USER=dds;cat%20/etc/shadow
may send us the encoded contents of the system's password
file after the results of the finger command.
Login: dds Name: Diomidis Spinellis
Directory: /home/dds Shell: /bin/bash
On since Wed Jun 30 12:18 (EET) on ttyp0
5 minutes 49 seconds idle
root:XXXXXXXXXXXXX:0:0:Charlie Root:/root:/bin/bash
bin:*:1:1:bin:/bin:
daemon:*:2:2:The Devil Himself:/sbin:
adm:*:3:4:adm:/var/adm:
lp:*:4:7:lp:/var/spool/lpd:
...
Scripting Guidelines
To avoid exploitation problems:
- Run the server as a non-priviledged user
- Maintain the server's host security
- Avoid scripting languages on web servers
- Do not trust form data
- Check all user data and remove all metacharacters
State Variable Manipulation
- The HTTP protocol is stateless
- A number of different mechanisms are used to store state:
- Cookies
- Hidden fields
- Parameters
- These entities are typically not protected
- Attackers can manipulate these entities to alter their identity or authorization
Cross-site Scripting
- Attacker stores script on victim site
- Attacker tricks user into executing script
- Victim user enters confidential data
- Attacker uses confidential data against victim user
Bibliography
-
Practical UNIX and Internet Security, 2nd Edition by Simson Garfinkel and Gene Spafford
- Ross Anderson.
Security Engineering: A Guide to Building Dependable Distributed Systems,
pages 367–371, 379–388.
John Wiley & Sons, New York, 2001.
- David Geer.
E-micropayements sweat the small stuff.
Computer, 37(8):19–22, August 2004.
- Dieter Gollmann.
Computer Security, pages 186–199.
John Wiley & Sons, New York, 1999.
- U. Homann, M. Rill, and
A. Wimmer.
Flexible value structures in banking.
Communications of the ACM, 47(5):34–36, May 2004.
- Michael Howard and
David LeBlanc.
Writing Secure Code, pages 413–438, 477–516.
Microsoft Press, Redmond, WA, second edition, 2003.
- Gary McGraw and
Edward W. Felten.
Securing Java: Getting Down to Business with Mobile Code.
Wiley, New York, 1999.
- Aviel D. Rubin, Daniel
Geer, and Marcus J. Ranum.
Web
Security Sourcebook.
John Wiley & Sons, New York, 1997.
- Victoria
Skoularidou and Diomidis Spinellis.
Security architectures for network clients (http://www.dmst.aueb.gr/dds/pubs/jrnl/2003-IMCS-clisec/html/cli-sec.html).
Information Management and Computer Security, 11(2):84–91,
2003.
Appendix A: Protecting the Internet Explorer
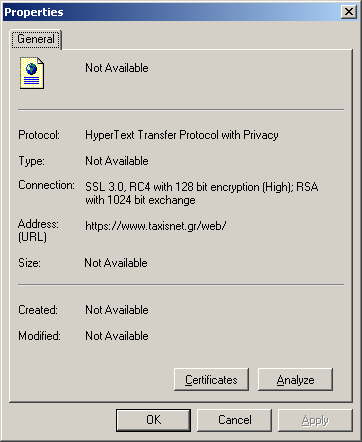
Information of a secure page
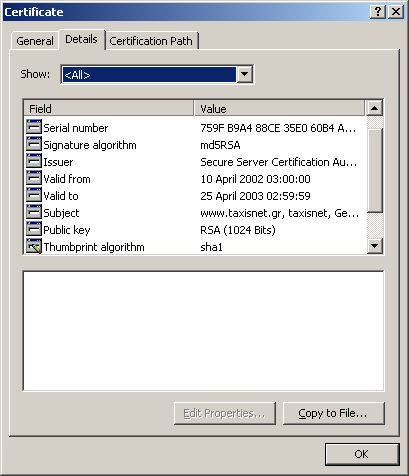
Page certificate information
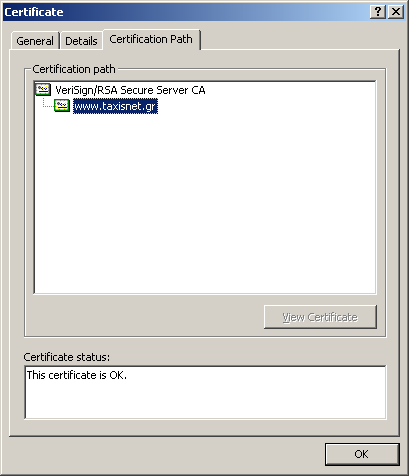
Certification path
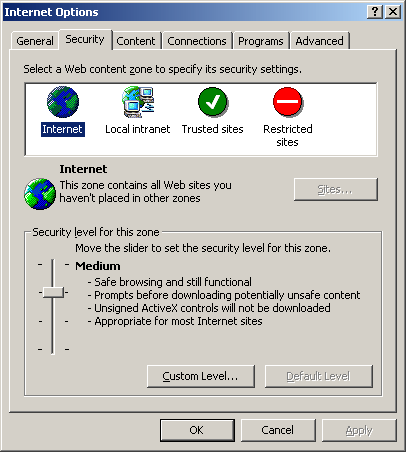
Basic security settings
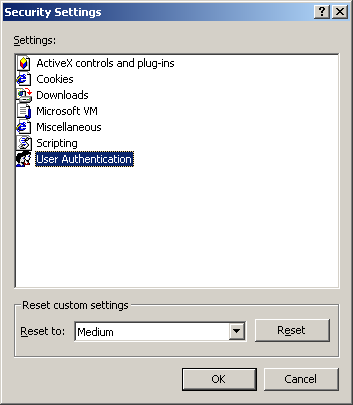
Tailored security settings
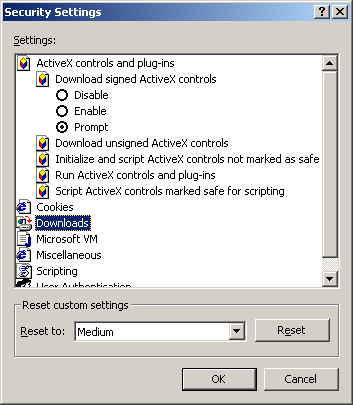
ActiveX controls
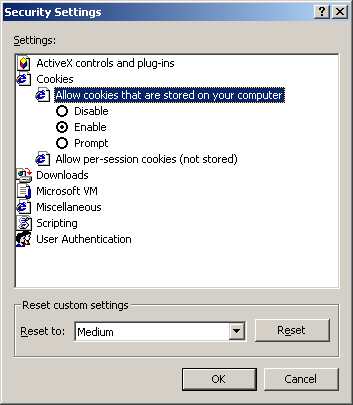
Cookies
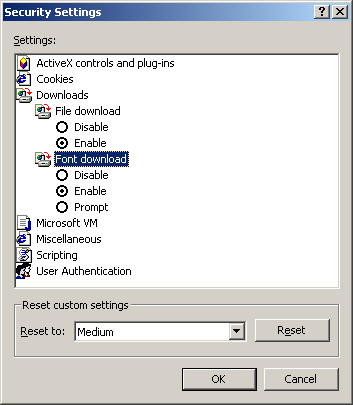
Downloads
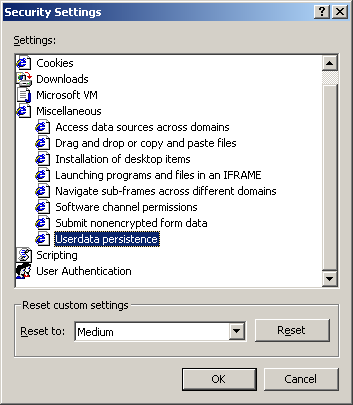
Microsoft extensions
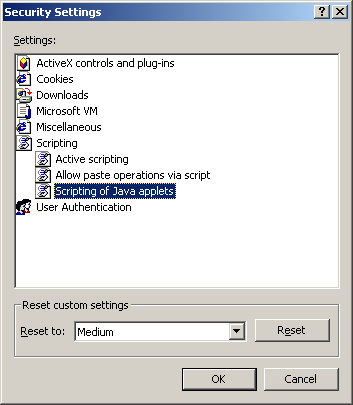
Scripting
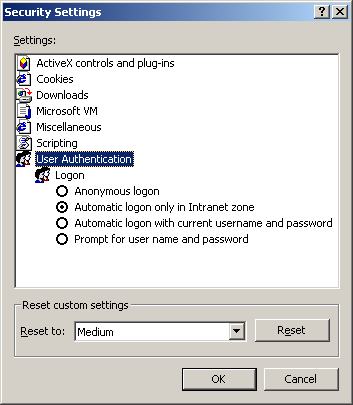
Authentication
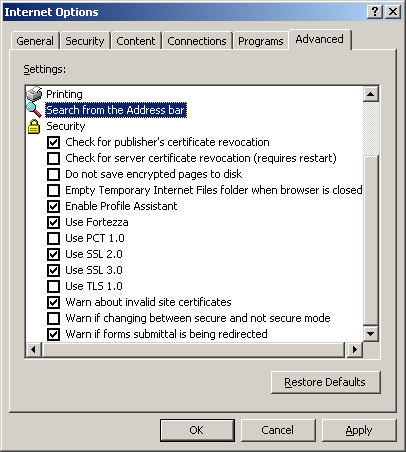
Security implementation
Appendix B: Protecting Mozilla
Mozilla places privacy and security and devotes a number of configuration
options for this task.
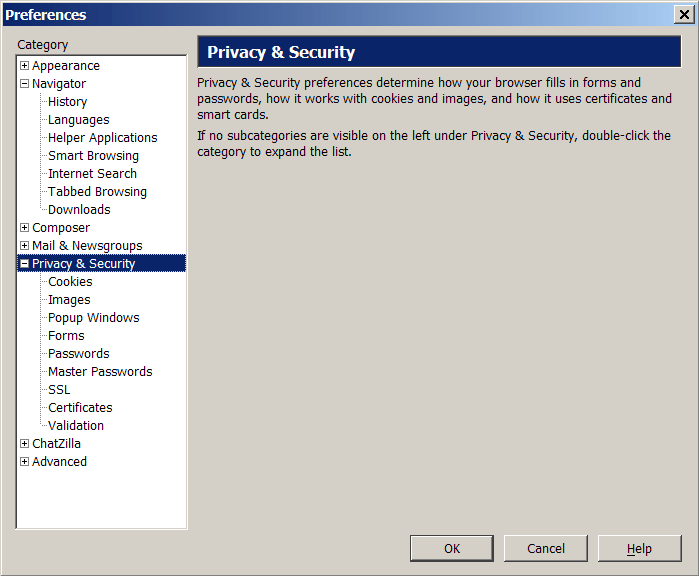
Privacy categories
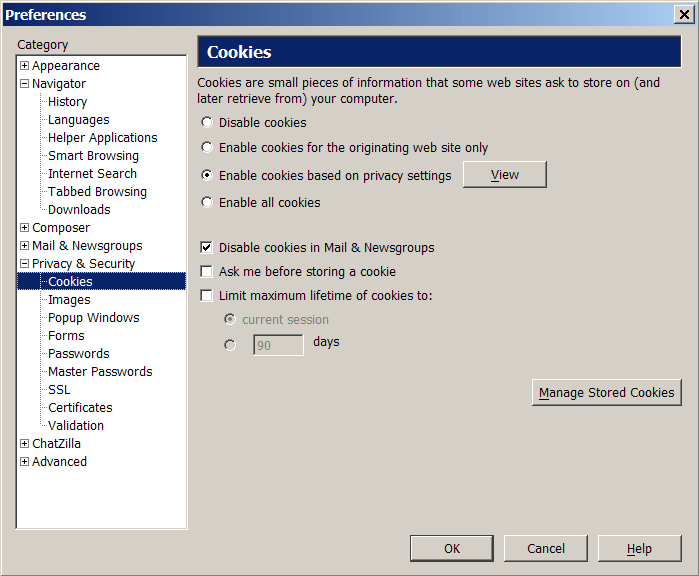
Cookie management
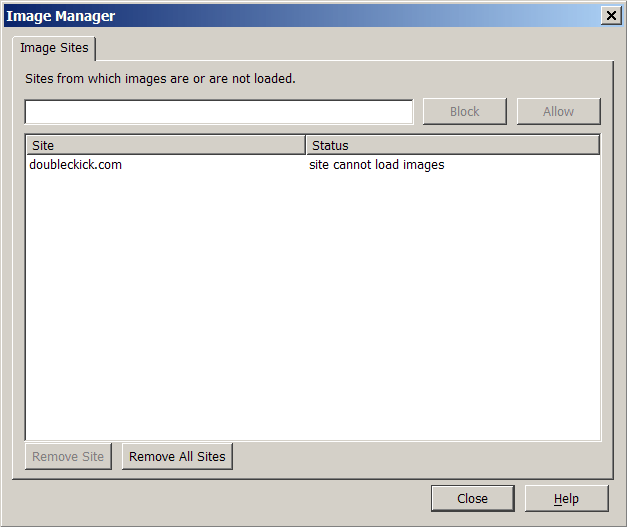
Image management
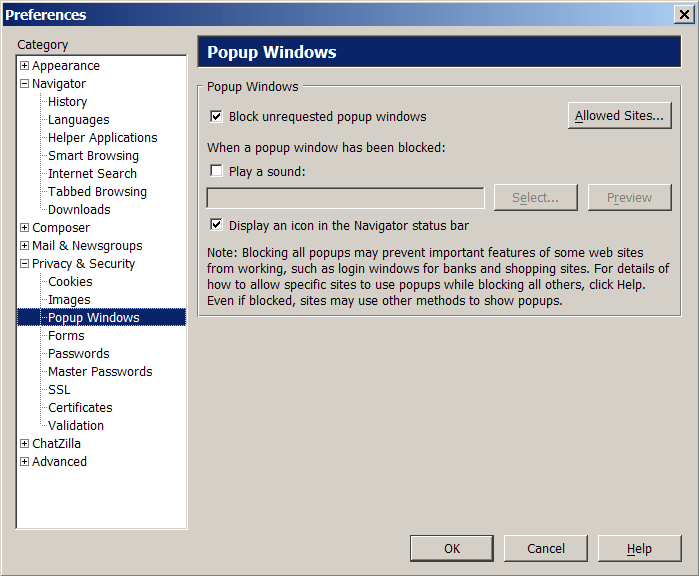
Popup window management
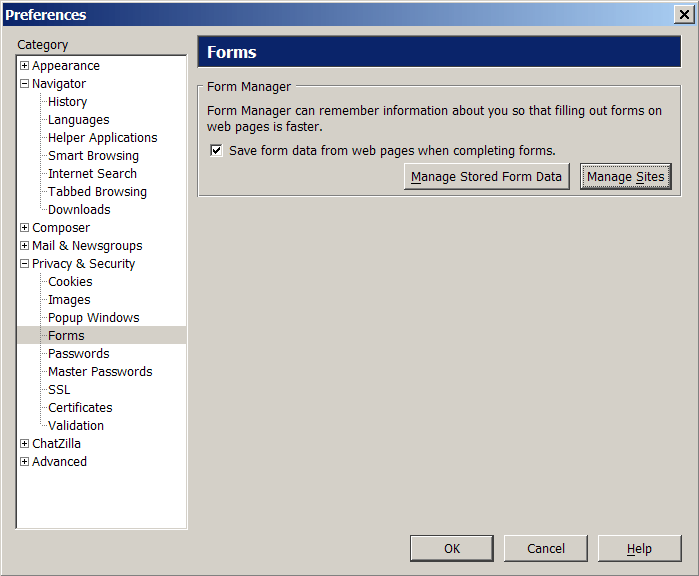
Form management
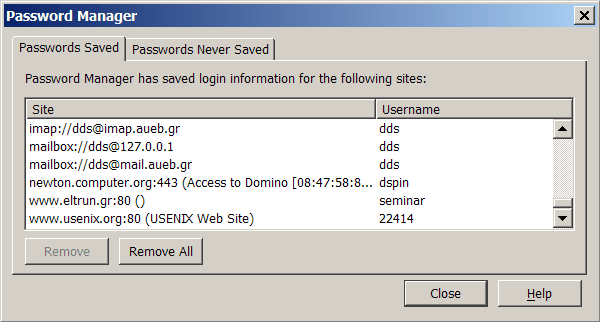
Password management
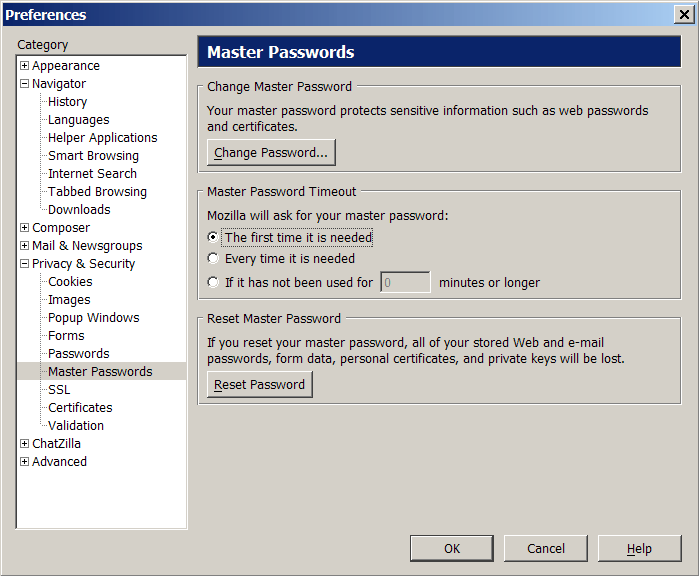
Master password
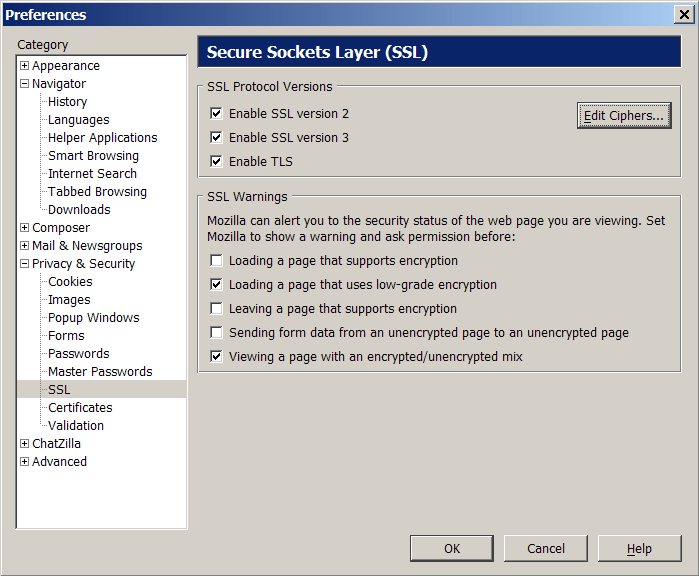
SSL details
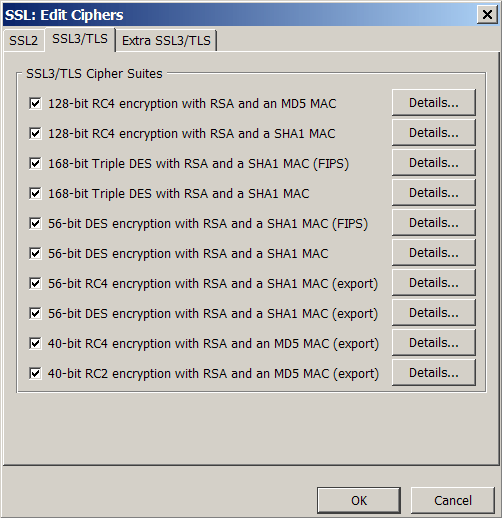
Cipher options
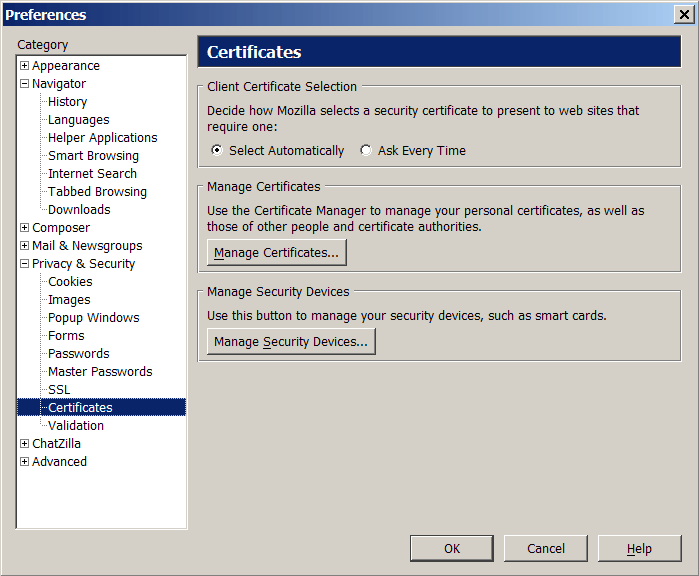
Certificate options
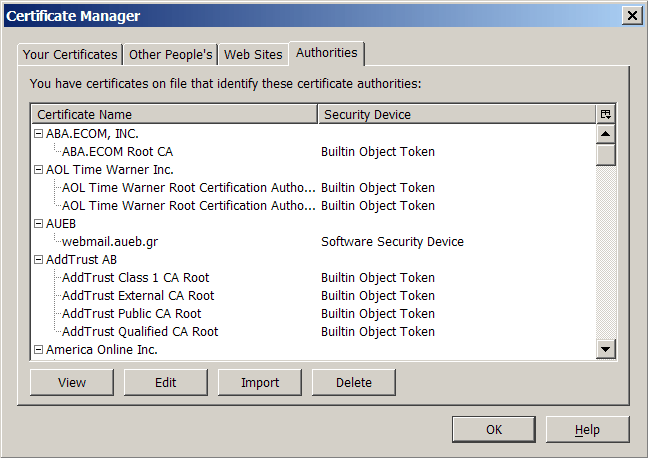
Certificate authorities
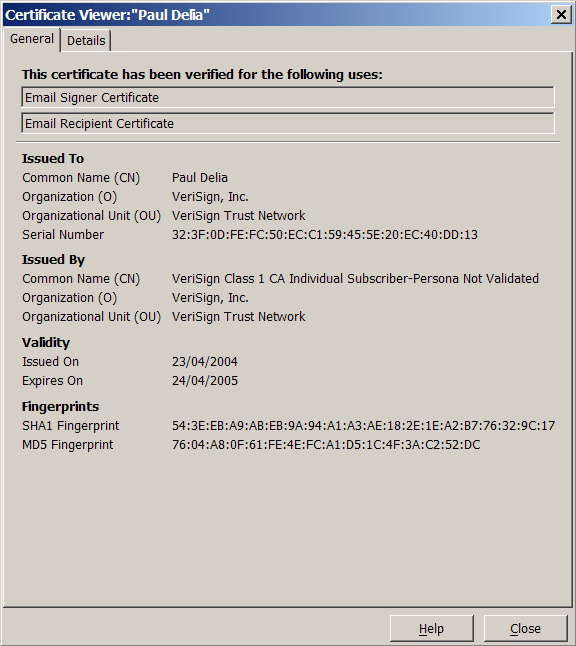
Personal certificate details
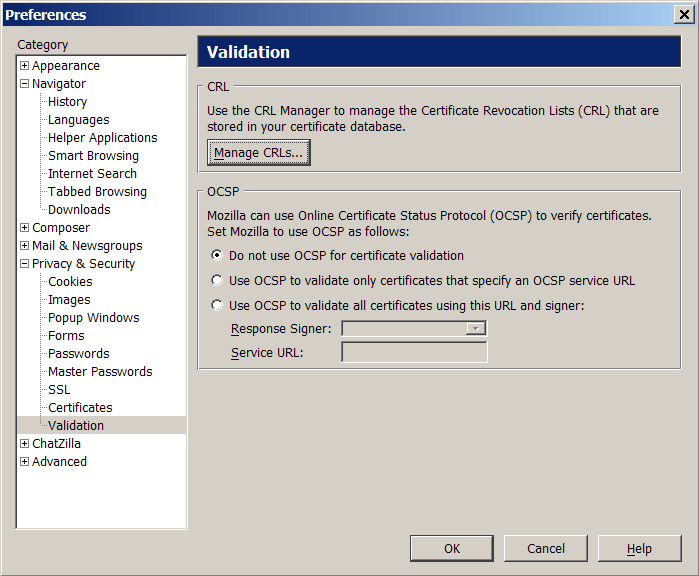
Certificate validation
Appendix C: Protecting the Netscape Navigator
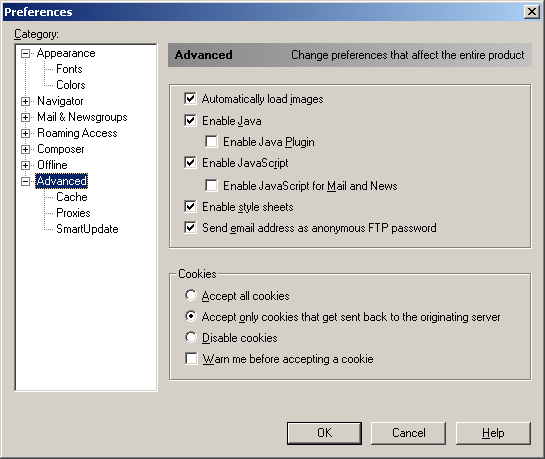
Executable content
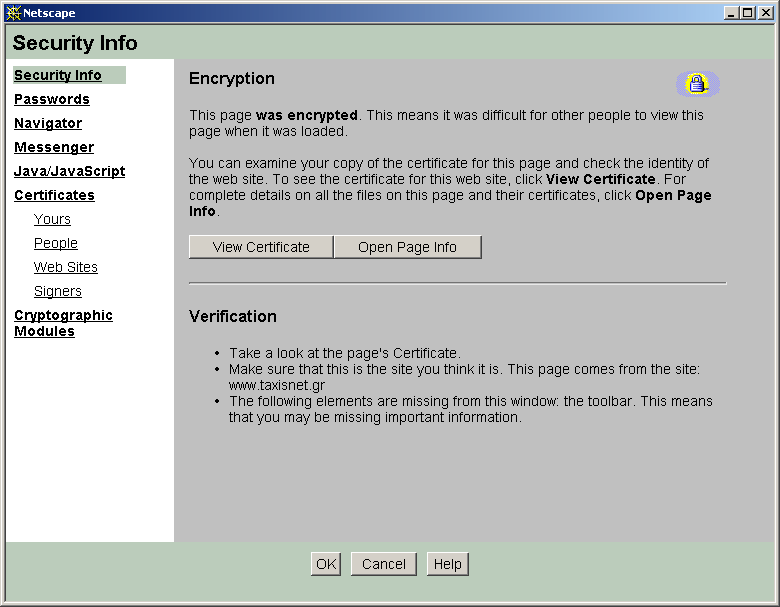
Content security information
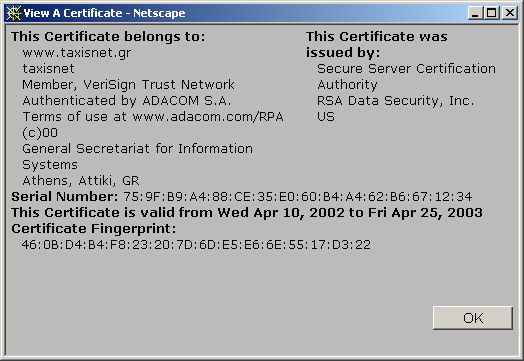
Certificate information
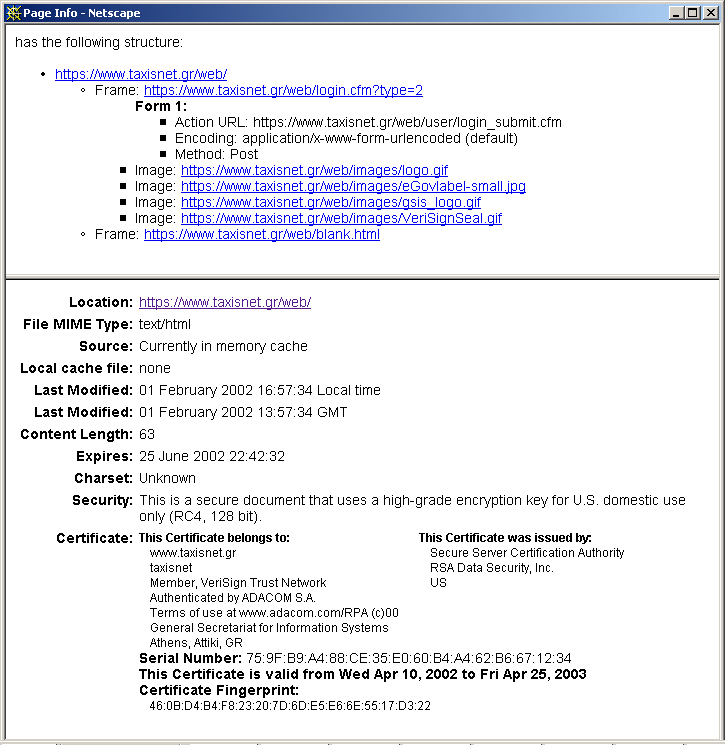
Secure page view
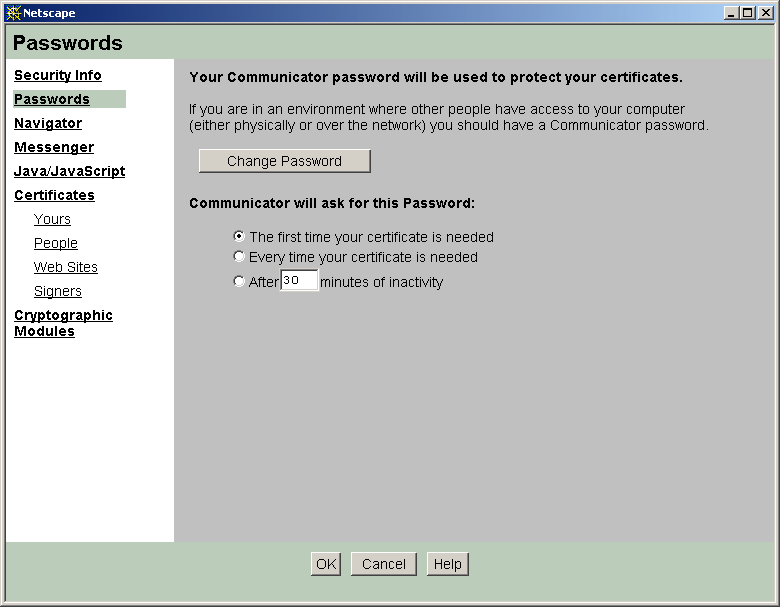
Password security
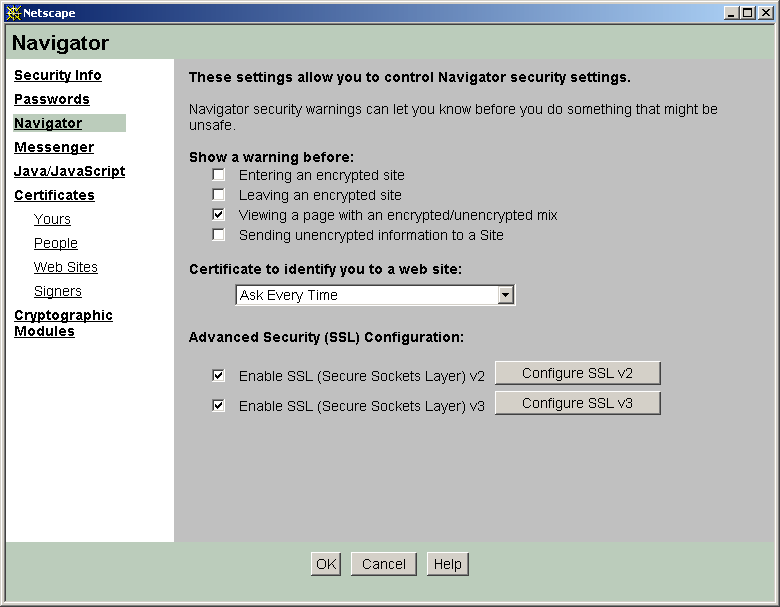
Browser settings
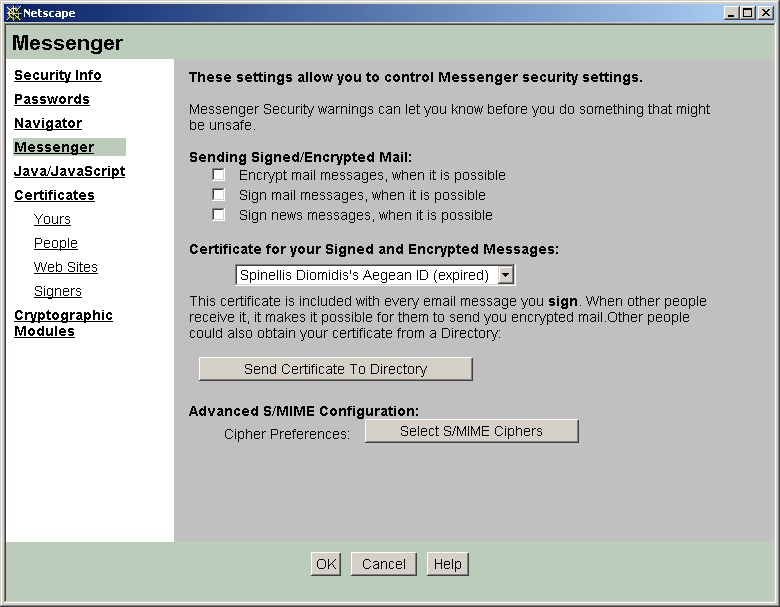
Mail settings
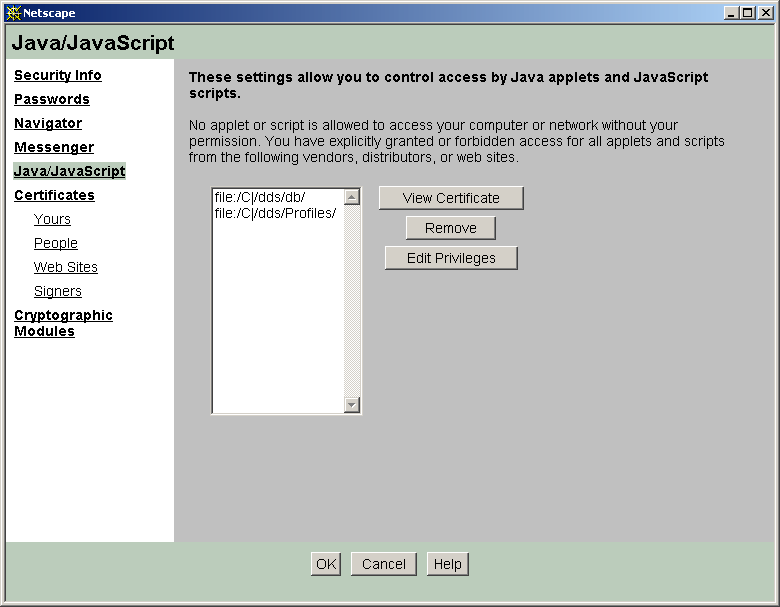
Signed executable content
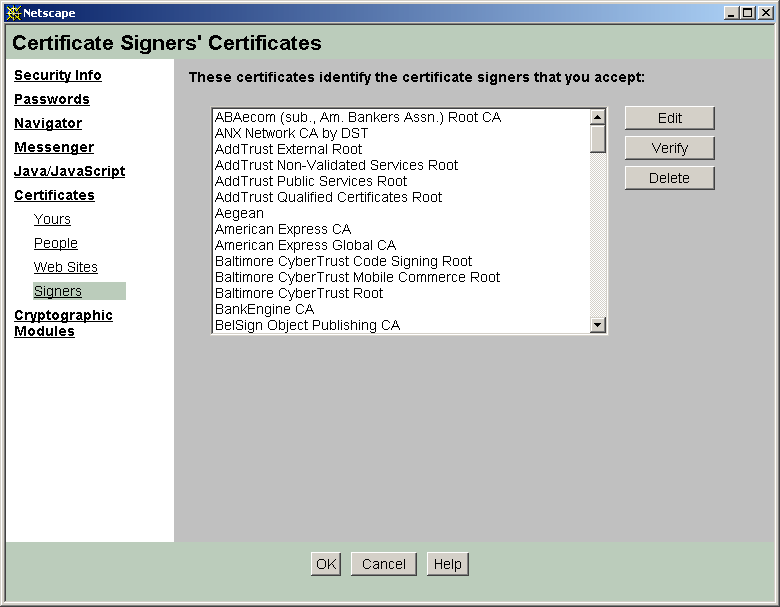
Certificates and CAs
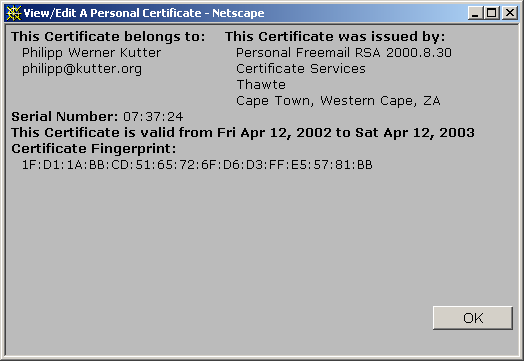
Personal Certificate
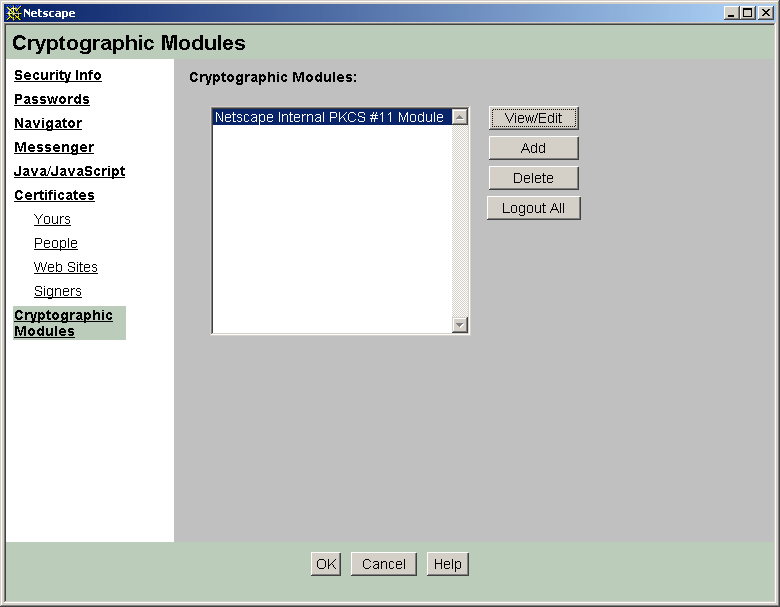
Cryptography
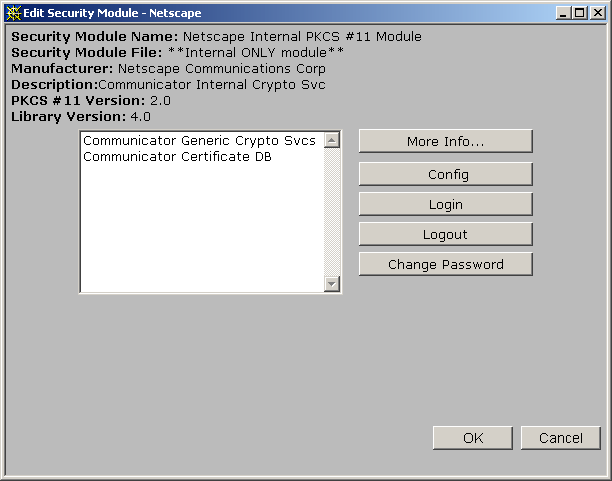
Cryptographic module access
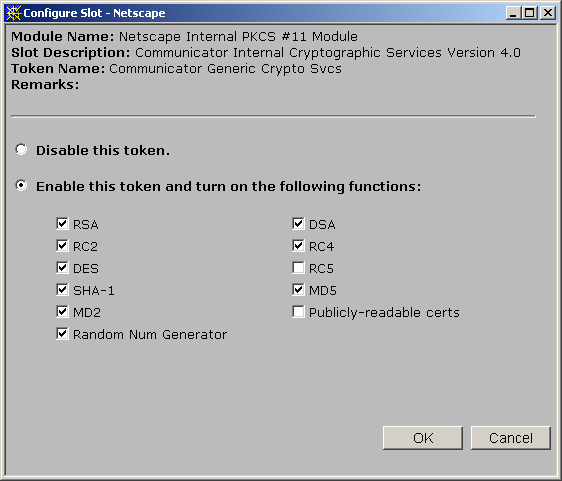
Cryptographic algorithms






































